This is from a Wednesday class on a particular day, and I thought it was detailed enough before, but obviously it wasn’t enough, and I did some studying on my own!
A buffer overflow is an anomaly that causes neighbouring memory locations to be overwritten when software writes data into a buffer that overflows the buffer’s capacity. In other words, excess information is passed into containers that do not have enough space, and this information eventually replaces the data in the adjacent containers.
An attacker can use a buffer overflow to modify a computer’s memory in order to corrupt or control the execution of a programme.
Let me use some impage from Internet(In this website: https://www.cloudflare.com/zh-cn/learning/security/threats/buffer-overflow/)
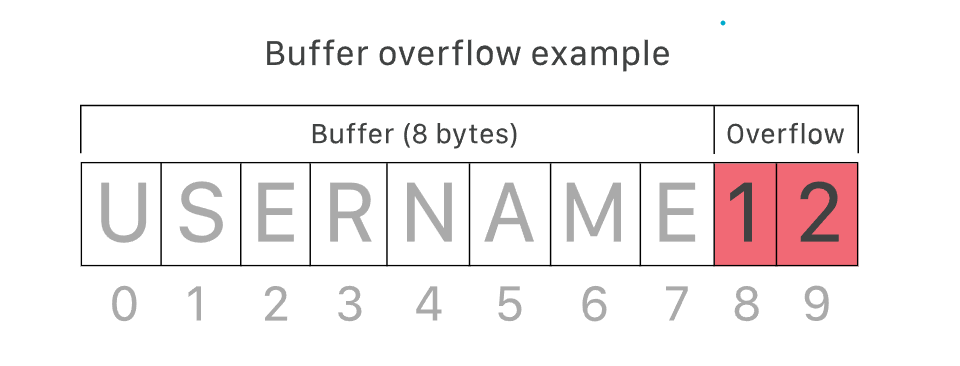
An attacker can deliberately feed carefully crafted input into a program, which will attempt to store that input in a buffer that is not large enough, so the input overwrites a portion of memory attached to the buffer space. If the memory layout of the program is well defined, the attacker can deliberately overwrite areas known to contain executable code. The attacker can then replace this code with executable code of their own, which can drastically change the way the program works.
For example, if the overwritten portion of memory contains a pointer (to an object in another location in memory), the attacker’s code can replace that code with another pointer to the exploit payload. This would transfer control of the entire programme to the attacker’s code.
Some programming languages are more susceptible to buffer overflows than others.C and C++ are two popular languages that are more vulnerable because they do not contain built-in protections against accessing or overwriting data in memory.Windows, Mac OSX, and Linux all contain code written in these two languages.
More modern languages such as Java, PERL, and C# have built-in features that can help reduce the chance of buffer overflows, but cannot completely prevent them.
There are many types of buffer overflow attacks that use different strategies and target different code segments. Here are some of the most well-known types.
Stack Overflow Attacks – This is the most common type of buffer overflow attack and involves a buffer overflow on the call stack.
1. Heap Overflow Attack – This type of attack targets data in an open pool of memory called the heap*.
2. Integer Overflow Attack – In an integer overflow, an arithmetic operation results in an integer that is too large for the type of integer to be stored as a result; this can result in a buffer overflow.
3. Unicode Overflow – A Unicode overflow creates a buffer overflow by inserting Unicode characters into input that requires ASCII characters. (ASCII and unicode are encoding standards that allow computers to represent text. For example, the letter “a” is represented by the number 97 in ASCII. While ASCII is only used to represent characters in Western languages, unicode can create characters for almost any written language on earth. Because there are more characters available in unicode, many unicode characters are larger than the largest ASCII characters.)
Here is an example code:
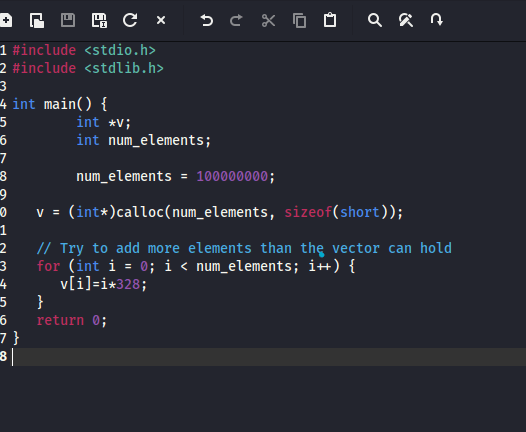
Let’s not write up where the holes are in this code and wait for a future me to discover them. Tip for myself: watch the length of ‘num_elements’!
